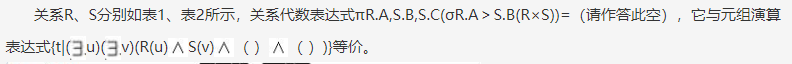
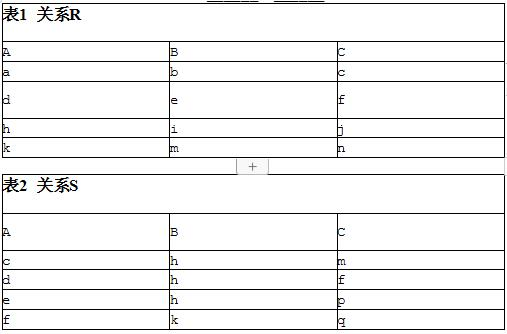
问题2:请将相关配置补充完整。总部防火墙firewall1部分配置如下。image.pngsystem-view[FIREWALL1] interface GigabitEthernet 1/0/2[FIREWALL1-GigabitEthernet1/0/2] ip address 192.168.1.1 24[FIREWALL1-GigabitEthernet1/0/2] quit[FIREWALL1] interface GigabitEthernet 1/0/1[FIREWALL1-GigabitEthernet1/0/1] ip address 202.1.3.1 24[FIREWALL1-GigabitEthernet1/0/1] quit# 配置接口加入相应安全区域。[FIREWALL1] (1)[FIREWALL1-zone-trust] (2)[FIREWALL1-zone-trust] quit[FIREWALL1] (3)[FIREWALL1-zone-untrust] (4)[FIREWALL1-zone-untrust] quit# 配置Trust域与Untrust域安全策略,允许封装前和解封后报文能通过[FIREWALL1] (5)[FIREWALL1-policy-security] rule name 1[FIREWALL1-policy-security-rule-1] source-zone trust[FIREWALL1-policy-security-rule-1] destination-zone untrust[FIREWALL1-policy-security-rule-1] source-address (6)[FIREWALL1-policy-security-rule-1] destination-address(7)[FIREWALL1-policy-security-rule-1] (9)[FIREWALL1-policy-security-rule-1] quit…..# 配置Local域与Untrust域安全策略,允许IKE协商报文能正常通过FIREWALL1。[FIREWALL1-policy-security] rule name 3[FIREWALL1-policy-security-rule-3] source-zone local[FIREWALL1-policy-security-rule-3] destination-zone untrust[FIREWALL1-policy-security-rule-3] source-address 202.1.3.1 32[FIREWALL1-policy-security-rule-3] destination-address 202.1.5.1 32[FIREWALL1-policy-security-rule-3] action permit[FIREWALL1-policy-security-rule-3] quit[FIREWALL1-policy-security] rule name 4[FIREWALL1-policy-security-rule-4] source-zone untrust[FIREWALL1-policy-security-rule-4] destination-zone local[FIREWALL1-policy-security-rule-4] source-address 202.1.5.1 32[FIREWALL1-policy-security-rule-4] destination-address 202.1.3.1 32[FIREWALL1-policy-security-rule-4] action permit[FIREWALL1-policy-security-rule-4] quit[FIREWALL1-policy-security] quit# 配置访问控制列表,定义需要保护数据流。[FIREWALL1] acl 3000[FIREWALL1-acl-adv-3000] rule (10)ip source 192.168.100.0 0.0.0.255 destination 192.168.200.00.0.0.255[FIREWALL1-acl-adv-3000] quit# 配置名称为tran1IPSec安全提议。[FIREWALL1] (11)[FIREWALL1-ipsec-proposal-tran1] encapsulation-mode tunnel[FIREWALL1-ipsec-proposal-tran1] transform esp[FIREWALL1-ipsec-proposal-tran1] esp authentication-algorithm sha2-256[FIREWALL1-ipsec-proposal-tran1] esp encryption-algorithm aes[FIREWALL1-ipsec-proposal-tran1] quit# 配置序号为10IKE安全提议。[FIREWALL1] ike proposal 10[FIREWALL1-ike-proposal-10] authentication-method pre-share[FIREWALL1-ike-proposal-10] authentication-algorithm sha2-256[FIREWALL1-ike-proposal-10] quit# 配置IKE用户信息表。[FIREWALL1] ike user-table 1[FIREWALL1-ike-user-table-1] user id-type ip (12) pre-shared-key Admin@gkys[FIREWALL1-ike-user-table-1] quit# 配置IKE Peer。[FIREWALL1] ike peer b[FIREWALL1-ike-peer-b] ike-proposal 10[FIREWALL1-ike-peer-b] user-table 1[FIREWALL1-ike-peer-b] quit# 配置名称为map_temp序号为1IPSec安全策略模板。[FIREWALL1] ipsec policy-template map_temp 1[FIREWALL1-ipsec-policy-template-map_temp-1] security acl (13)[FIREWALL1-ipsec-policy-template-map_temp-1] proposal tran1[FIREWALL1-ipsec-policy-template-map_temp-1] ike-peer b[FIREWALL1-ipsec-policy-template-map_temp-1] reverse-route enable[FIREWALL1-ipsec-policy-template-map_temp-1] quit# 在IPSec安全策略map1中引用安全策略模板map_temp。[FIREWALL1] ipsec policy map1 10 isakmp template map_temp# 在接口GigabitEthernet 1/0/1上应用安全策略map1。[FIREWALL1] interface GigabitEthernet 1/0/1[FIREWALL1-GigabitEthernet1/0/1] ipsec policy map1[FIREWALL1-GigabitEthernet1/0/1] quit[Switch] acl number 2001[Switch-acl-basic-2001] rule permit source 172.16.105.0 0.0.0.255 //允许172.16.105.0/24网段所有用户在任意时间都可以访问FTP服务器[Switch-acl-basic-2001] rule permit source 172.16.107.0 0.0.0.255 time-range tr1 //限制172.16.107.0/24网段所有用户只能在tr1时间段定义时间范围内访问FTP服务器[Switch-acl-basic-2001] rule deny source any //限制其他用户不可以访问FTP服务器[Switch-acl-basic-2001] quit
(1),firewall,zone,trust (2)add,interface,GigabitEthernet,1/0/2(3) firewall,zone,untrust (4) add,interface,GigabitEthernet,1/0/1 (5) security-policy (6), 192.168.100.0,24(7) 192.168.200.0,24 , (8) action permit
(9)action permit (10) permit(11) ipsec,proposal,tran1 (12) 202.1.5.1(13)3000
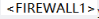
ystem-view[FIREWALL1] interface GigabitEthernet 1/0/2[FIREWALL1-GigabitEthernet1/0/2] ip address 192.168.1.1 24[FIREWALL1-GigabitEthernet1/0/2] quit[FIREWALL1] interface GigabitEthernet 1/0/1[FIREWALL1-GigabitEthernet1/0/1] ip address 202.1.3.1 24[FIREWALL1-GigabitEthernet1/0/1] quit# 配置接口加入相应安全区域。[FIREWALL1] firewall zone trust[FIREWALL1-zone-trust] add interface GigabitEthernet 1/0/2[FIREWALL1-zone-trust] quit[FIREWALL1] firewall zone untrust[FIREWALL1-zone-untrust] add interface GigabitEthernet 1/0/1[FIREWALL1-zone-untrust] quit2. 配置安全策略,允许私网指定网段进行报文交互。# 配置Trust域与Untrust域安全策略,允许封装前和解封后报文能通过[FIREWALL1] security-policy[FIREWALL1-policy-security] rule name 1[FIREWALL1-policy-security-rule-1] source-zone trust[FIREWALL1-policy-security-rule-1] destination-zone untrust[FIREWALL1-policy-security-rule-1] source-address 192.168.100.0 24[FIREWALL1-policy-security-rule-1] destination-address 192.168.200.0 24[FIREWALL1-policy-security-rule-1] action permit[FIREWALL1-policy-security-rule-1] quit…..# 配置Local域与Untrust域安全策略,允许IKE协商报文能正常通过FIREWALL1。[FIREWALL1-policy-security] rule name 3[FIREWALL1-policy-security-rule-3] source-zone local[FIREWALL1-policy-security-rule-3] destination-zone untrust[FIREWALL1-policy-security-rule-3] source-address 202.1.3.1 32[FIREWALL1-policy-security-rule-3] destination-address 202.1.5.1 32[FIREWALL1-policy-security-rule-3] action permit[FIREWALL1-policy-security-rule-3] quit[FIREWALL1-policy-security] rule name 4[FIREWALL1-policy-security-rule-4] source-zone untrust[FIREWALL1-policy-security-rule-4] destination-zone local[FIREWALL1-policy-security-rule-4] source-address 202.1.5.1 32[FIREWALL1-policy-security-rule-4] destination-address 202.1.3.1 32[FIREWALL1-policy-security-rule-4] action permit[FIREWALL1-policy-security-rule-4] quit[FIREWALL1-policy-security] quit3. 配置IPSec隧道。# 配置访问控制列表,定义需要保护数据流。[FIREWALL1] acl 3000[FIREWALL1-acl-adv-3000] rule permit ip source 192.168.100.0 0.0.0.255 destination 192.168.200.00.0.0.255[FIREWALL1-acl-adv-3000] quit# 配置名称为tran1IPSec安全提议。[FIREWALL1] ipsec proposal tran1[FIREWALL1-ipsec-proposal-tran1] encapsulation-mode tunnel[FIREWALL1-ipsec-proposal-tran1] transform esp[FIREWALL1-ipsec-proposal-tran1] esp authentication-algorithm sha2-256[FIREWALL1-ipsec-proposal-tran1] esp encryption-algorithm aes[FIREWALL1-ipsec-proposal-tran1] quit# 配置序号为10IKE安全提议。[FIREWALL1] ike proposal 10[FIREWALL1-ike-proposal-10] authentication-method pre-share[FIREWALL1-ike-proposal-10] authentication-algorithm sha2-256[FIREWALL1-ike-proposal-10] quit# 配置IKE用户信息表。[FIREWALL1] ike user-table 1[FIREWALL1-ike-user-table-1] user id-type ip 202.1.5.1 pre-shared-key Admin@gkys[FIREWALL1-ike-user-table-1] quit# 配置IKE Peer。[FIREWALL1] ike peer b[FIREWALL1-ike-peer-b] ike-proposal 10[FIREWALL1-ike-peer-b] user-table 1[FIREWALL1-ike-peer-b] quit# 配置名称为map_temp序号为1IPSec安全策略模板。[FIREWALL1] ipsec policy-template map_temp 1[FIREWALL1-ipsec-policy-template-map_temp-1] security acl 3000[FIREWALL1-ipsec-policy-template-map_temp-1] proposal tran1[FIREWALL1-ipsec-policy-template-map_temp-1] ike-peer b[FIREWALL1-ipsec-policy-template-map_temp-1] reverse-route enable[FIREWALL1-ipsec-policy-template-map_temp-1] quit# 在IPSec安全策略map1中引用安全策略模板map_temp。[FIREWALL1] ipsec policy map1 10 isakmp template map_temp# 在接口GigabitEthernet 1/0/1上应用安全策略map1。[FIREWALL1] interface GigabitEthernet 1/0/1[FIREWALL1-GigabitEthernet1/0/1] ipsec policy map1[FIREWALL1-GigabitEthernet1/0/1] quit
在几种不同类型的软件维护中,通常情况下()所占工作量最大。
在()中,项目经理的权力是最小的。
在项目实施的过程中,项目经理通过项目周报中的项目进度分析图表发现机房施工进度有延期风险。项目经理立即组织相关人员进行分析,下达了关于改进措施的书面指令。该指令属于( )

The IT service manager resigns from a project that meets the scheduleand budget. After hiring an alternativenew manager, the team is opposed to the comments from the new manager. The team is at () developmentstages。
()is closet to Deming's definition of Quality。
The IT service manager has learned that a software canimprove the efficiency of current and future project tasks. Because the software is fresh to the Company. Theengineer is not familiar with the software. The lT service manager decides to send the highest level engineero attend the external training course. The proiect manager uses () risk strategies。
The process control charts are used ()。